The Android developer who raised the ire of a mobile-phone monitoring company last week is on the attack again, producing a video of how the Carrier IQ software secretly installed on millions of mobile phones reports most everything a user does on a phone.
Though the software is installed on most modern Android, BlackBerry and Nokia phones, Carrier IQ was virtually unknown until 25-year-old Trevor Eckhart of Connecticut analyzed its workings, revealing that the software secretly chronicles a user’s phone experience — ostensibly so carriers and phone manufacturers can do quality control.
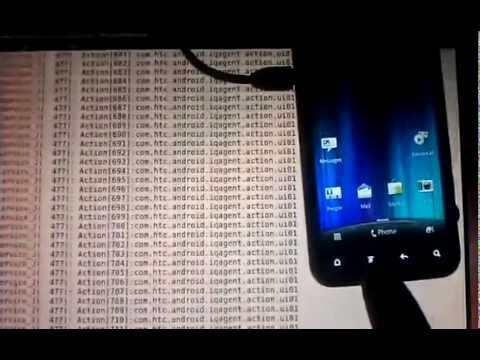
But now he’s released a video actually showing the logging of text messages, encrypted web searches and, well, you name it.
Eckhart labeled the software a “rootkit,” and the Mountain View, California-based software makerthreatened him with legal action and huge money damages. The Electronic Frontier Foundation came to his side last week, and the company backed off on its threats. The company told Wired.com last week that Carrier IQ’s wares are for “gathering information off the handset to understand the mobile-user experience, where phone calls are dropped, where signal quality is poor, why applications crash and battery life.”
The company denies its software logs keystrokes. Eckhart’s 17-minute video clearly undercuts that claim.
In a Thanksgiving post, we mentioned this software as one of nine reasons to wear a tinfoil hat.
The video shows the software logging Eckhart’s online search of “hello world.” That’s despite Eckhart using the HTTPS version of Google which is supposed to hide searches from those who would want to spy by intercepting the traffic between a user and Google.
Cringe as the video shows the software logging each number as Eckhart fingers the dialer.
“Every button you press in the dialer before you call,” he says on the video, “it already gets sent off to the IQ application.”
From there, the data — including the content of text messages — is sent to Carrier IQ’s servers, in secret.
By the way, it cannot be turned off without rooting the phone and replacing the operating system. And even if you stop paying for wireless service from your carrier and decide to just use Wi-Fi, your device still reports to Carrier IQ.
It’s not even clear what privacy policy covers this. Is it Carrier IQ’s, your carrier’s or your phone manufacturer’s? And, perhaps, most important, is sending your communications to Carrier IQ a violation of the federal government’s ban on wiretapping?
And even more obvious, Eckhart wonders why aren’t mobile-phone customers informed of this rootkit and given a way to opt out?






Comment